Overview
Install and configure Identity Guardian using Zebra DNA Cloud (navigate to My Apps > Zebra Collection) or through an Enterprise Mobility Management (EMM) system. Administrators establish usage policies and controls for Identity Guardian via Managed Configurations. This enables companies to personalize device restrictions and access.
Through Zebra DNA Cloud's dashboard, administrators gain insight into user activities such as sign-in/sign-out events and usage durations, promoting user accountability.
Identity Guardian simplifies application authentication by integrating with your organization's identity provider (IdP). It enables single sign-on (SSO) where users only need to log in once and it handles subsequent application log-ins, streamlining the process.
Notes:
- Identity Guardian, being an application that must be sideloaded, is not operational when the device is started in safe mode. Therefore, Zebra discourages administrators from starting devices in safe mode. To disable safe mode, apply the corresponding XML through your EMM or scan the relevant barcode using the StageNow client on the device. The XML and StageNow barcode are made available depending on your Android version:
- When using the 42Gears EMM system, apps installed via Zebra DNA Cloud in app update mode must be set as high priority.
Requirements
Identity Guardian requirements:
- Zebra devices running Android 11 or higher are supported. See Zebra Support Portal for the supported devices.
- For biometric authentication, a front-facing camera is required on the device
- Licenses:
- An Identity Guardian license is required for advanced features including facial biometric authentication, Single Sign-On (SSO) support and device API support. See Licensing.
- Zebra Professional-series devices require a Mobility DNA Enterprise license for basic functionality
- An Enterprise Mobility Management (EMM) system, such as Zebra DNA Cloud or a third party system, that supports Managed Configurations (also known as Managed App Configurations) is required to configure Identity Guardian on the device.
- After installation on the device, Identity Guardian must be launched for the configurations to be applied.
- Single sign-on (SSO) support: Compatibility with Microsoft Entra ID (formerly Azure Active Directory) and PingID platforms using OAUTH and OAUTH+OIDC authentication protocols.
Download
Download and install Identity Guardian from the Zebra support portal.
EMM
Deploy and configure Identity Guardian on devices using an Enterprise Mobility Management (EMM) system, such as Zebra DNA Cloud or a third party system, which supports Managed Configurations.
After installation, Identity Guardian must be launched for the configurations to take effect.
The EMM system may offer the option to auto-launch the app. If this option is not available, the following commands may be used to launch Identity Guardian:
For Android, such as from another app, use this command:
adb shell am start -n com.zebra.mdna.els/com.zebra.mdna.els.userEnrollment.activity.EnrollmentActivityFor an EMM, such as VMware Workspace ONE UEM (AirWatch), use this command to launch via intent:
mode=explicit,broadcast=false,action=android.intent.action.MAIN,package=com.zebra.mdna.els,class=com.zebra.mdna.els.userEnrollment.activity.EnrollmentActivity
Generic procedure to setup Identity Guardian using an EMM:
- Enroll the devices to the EMM.
- Upload the Identity Guardian APK to the EMM, for example via Android Enterprise or the EMM's App Store. Make sure to auto-launch the app after installation.
- Create a new application policy to configure the appropriate Identity Guardian settings. Consider the following:
- For shared devices, create two distinct profiles:
- Enrollment - This is required when implementing facial biometrics. It generates unique user barcodes for authentication. To configure this, go to Usage Mode > Application Mode and select Enrollment.
- Authentication - This configures the authentication methods for users to sign into the device. To configure this, go to Usage Mode > Application Mode and select Authentication.
- For personally assigned devices, a single profile encompasses both enrollment and authentication configurations. To configure this, go to Usage Mode > Application Mode and select Personally Assigned.
- For shared devices, create two distinct profiles:
- Assign and apply the application policy to the devices. For shared devices, apply the Enrollment profile first.
- For enrollment, follow the steps on the device to proceed through user enrollment. These steps are based on the Enrollment Configuration settings from step 3.
- For shared devices, refer to shared device user enrollment.
- For personally assigned devices, refer to personl device user enrollment.
- For shared devices, create the Authentication policy and apply this policy to the devices. For personally assigned devices, skip to step 7.
- After device enrollment, the Identity Guardian authentication screen is displayed. The user is now ready to sign into the device based on Authentication Configuration settings from step 3. Refer to Device Sign In.
In the following subsections, video demonstrations are available tailored for specific EMMs.
Zebra DNA Cloud
This section provides video demonstrations to guide through the process of setting up Identity Guardian, in this case on a shared device, using the Zebra DNA Console.
For shared devices, two separate configuration profiles can be created based on the Application Mode selected under the Usage Mode section:
- Enrollment - Use this mode if facial biometrics is utilized to create unique user barcodes for authentication.
- Authentication - This configures the authentication methods employed for users to sign into the device.
This first video guides through the process of creating and deploying an enrollment profile, specifically for a shared device. Learn how to define configurations for a user's first-time enrollment, including registering facial features, obtaining user role data, setting up a pin code, and more.
Note: For personally assigned devices, select Personally Assigned from Application Mode under the Usage Mode section. This creates a profile encompaassing both enrollment and authentication configurations.
This second video walks through the process of creating and deploying an authentication profile, specifically for a shared device. It guides through the process of establishing configurations for user authentication each time a user signs into the device. These configurations include scanning a barcode, setting up SSO, defining the passcode, among others. The enrollment profile, created from the previous video, can be used as a template to modify and create this authentication profile.
This video demonstrates various scenarios of user device authentication. In this example, one group of authentication settings is applied to a shared device with the following configurations:
- Comparison source: Barcode
- Primary authentication: SSO
- Secondary authentication: Passcode
- Fallback authentication: Admin bypass passcode
SOTI MobiControl
This video guides through the process of setting up Identity Guardian using SOTI MobiControl, specifically for shared devices. It provides a guide to deploy the Identity Guardian APK file, automatically launch the app, create and apply an enrollment profile, as well as create and apply an authentication profile for shared devices.
Note: For personally assigned devices, select Personally Assigned from Application Mode under the Usage Mode section. This creates a profile encompassing both enrollment and authentication configurations.
42Gears SureMDM
This videos walks through the process of setting up Identity Guardian using SureMDM by 42Gears, specifically for personally assigned devices. It provides a guide to deploy the Identity Guardian APK file, automatically launch the app, and create a policy to configure the desired settings for enrollment and authentication on personally assigned devices.
Note: For shared devices, create two separate configuration profiles according to the selected Application Mode under the Usage Mode section:
- Enrollment - Use this mode if facial biometrics is utilized to create unique user barcodes for authentication.
- Authentication - This configures the authentication methods employed for users to sign into the device.
SSO
Identity Guardian integrates with identity providers (IdPs) simplifying authentication by only requiring users to log in once, and then leveraging single sign-on (SSO) to streamline the process. This single login grants users to gain access to multiple applications, eliminating the need to keep track of multiple logins for each app.
Supported identity providers:
For authenticating users with SSO, the Microsoft Authenticator and Custom Chrome Tabs are supported to communicate with SSO as the broker.
See SSO Requirements.
Microsoft Entra ID
This section provides guidance to integrate Identity Guardian with Microsoft Entra ID (formerly Azure Active Directory):
I. Register Zebra Identity Guardian
II. Configure SSO for Shared Devices
III. Configure Microsoft Authenticator App
IV. Configure Zebra Identity Guardian App
I. Register Zebra Identity Guardian
To establish a trust relationship between Identity Guardian and the Microsoft identity platform, register Zebra Identity Guardian as an Android application in Microsoft Entra ID (IdP). Consult Microsoft's documentation for guidance on registering an application with the Microsoft identity platform.
Please ensure to enter or select the following when registering Identity Guardian:
- For the supported account type, select "Single tenant."
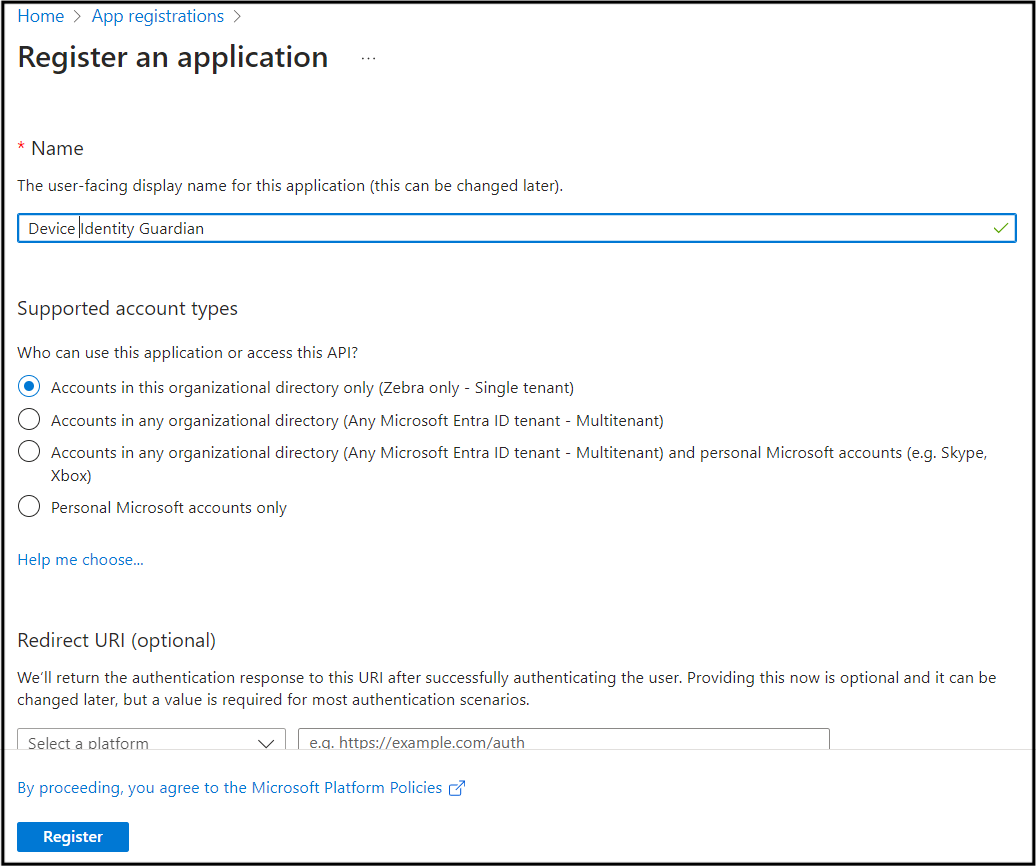
- When configuring the Android app, enter the following:
- Package name: com.zebra.mdna.els
- Signature hash: KqmK9tYXpw+eW2lke7US3iG9EAQ=
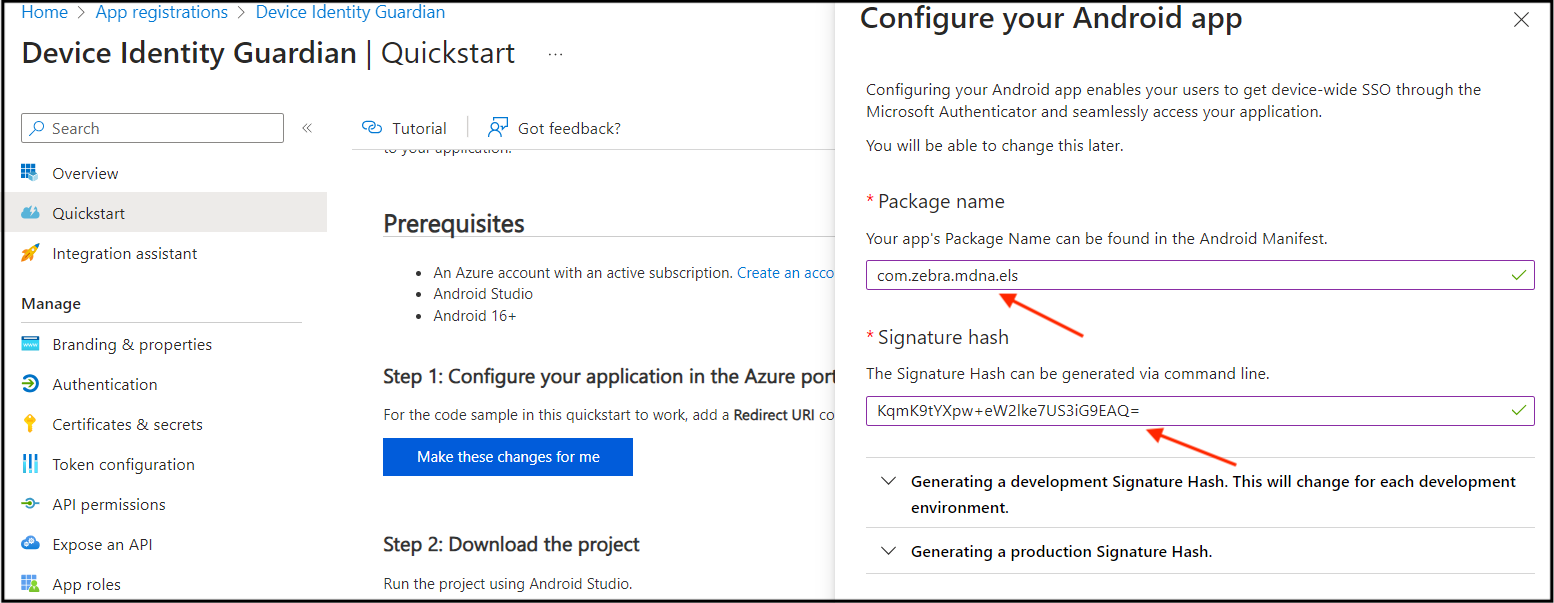
- Download the code sample and save the file as
auth_config_single_account.json. This will be used in a subsequent step to configure the app settings on the device.
II. Configure SSO for Shared Devices
If Microsoft Authenticator is used for single sign-on (SSO) on shared devices, it is possible to integrate a third-party device compliance partner solution with Microsoft Intune. This allows for the collection of device compliance data in conjunction with Intune's own compliance results. The combined data can be used to formulate access policies, providing enhanced protection for your organization and its data. Examples of third-party device compliance partners include solutions such as SOTI MobiControl, VMware Workspace ONE UEM (formerly AirWatch), and others. Consult your EMM or Microsoft's documentation for guidance on adding a third-party device compliance partner in Intune.
III. Configure Microsoft Authenticator App
For optimal use of shared device mode with SSO through Microsoft Authenticator, ensure the Microsoft Authenticator app is installed on the devices. This facilitates automatic SSO single sign-in and single sign-out across apps on the device.
To install and configure Microsoft Authenticator app:
Download and install the Microsoft Authenticator app from Google Play via an EMM, such as SOTI MobiControl or VMware Workspace ONE UEM.
In the EMM, enable Shared Device Mode and enter the Shared Device Mode Tenant Identifier (obtained from the Microsoft Entra ID).
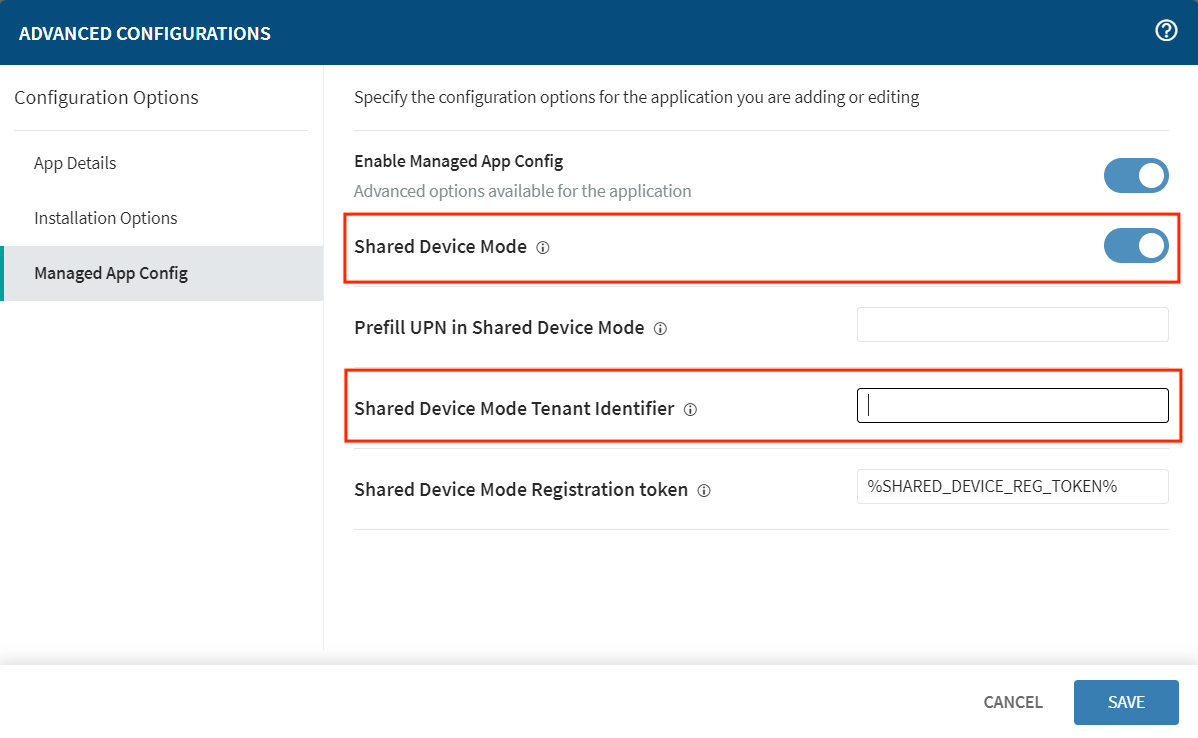
SOTI MobiControl Managed App Config
IV. Configure Zebra Identity Guardian App
To enable user access to the device through SSO, install and set up Identity Guardian on the devices:
Deploy and install Zebra Identity Guardian app on the devices.
Launch the app using an EMM. This step must be performed at least once.
Enter the Managed Configuration settings for the app via your EMM:
Select the application mode:
- Application Mode: Authentication
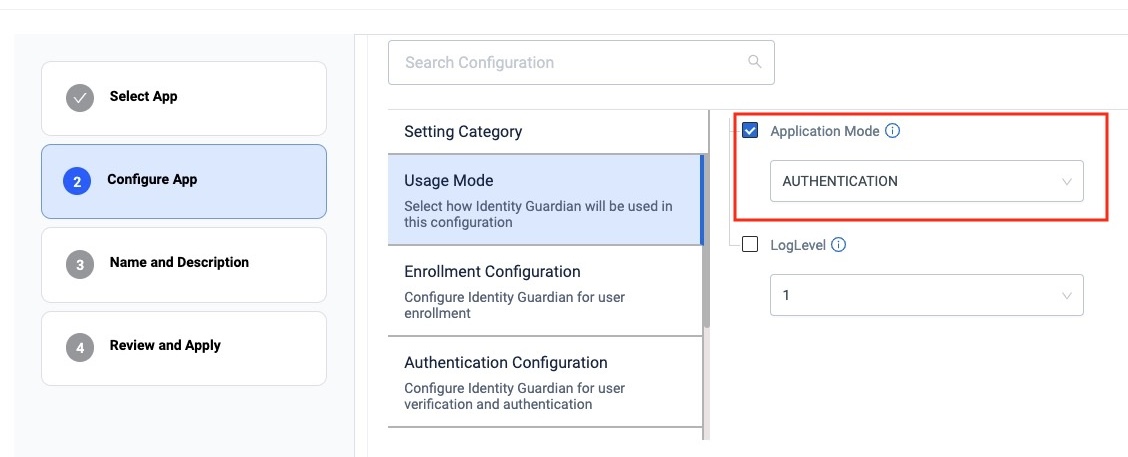 zDNA Cloud Managed Config
zDNA Cloud Managed Config
- Application Mode: Authentication
Configure the Verification Setup to validate the user access:
- Primary Authentication Factor: SSO
- Secondary Authentication Factor: [Select FACE, PASSCODE, SSO or NONE]
- Fallback Authentication Factor: [Select FACE, PASSCODE, NONE, SSO or ADMIN BYPASS PASSCODE]
- Primary Authentication Timeout: [Enter value in ms, e.g. "300000"]
- Fallback Authentication Timeout: [Enter value in ms, e.g. "300000"]
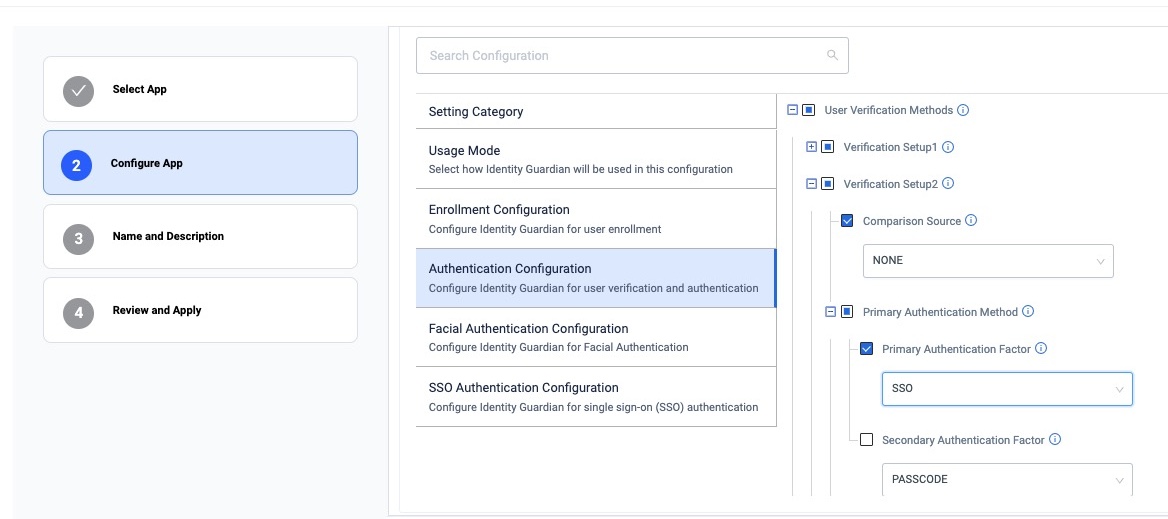 zDNA Cloud Managed Config
zDNA Cloud Managed Config
Configure the Lock-screen Event options:
- On Unlock:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On Reboot:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On AC power connected:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On AC power disconnected:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On device manual check in:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On user change: - Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
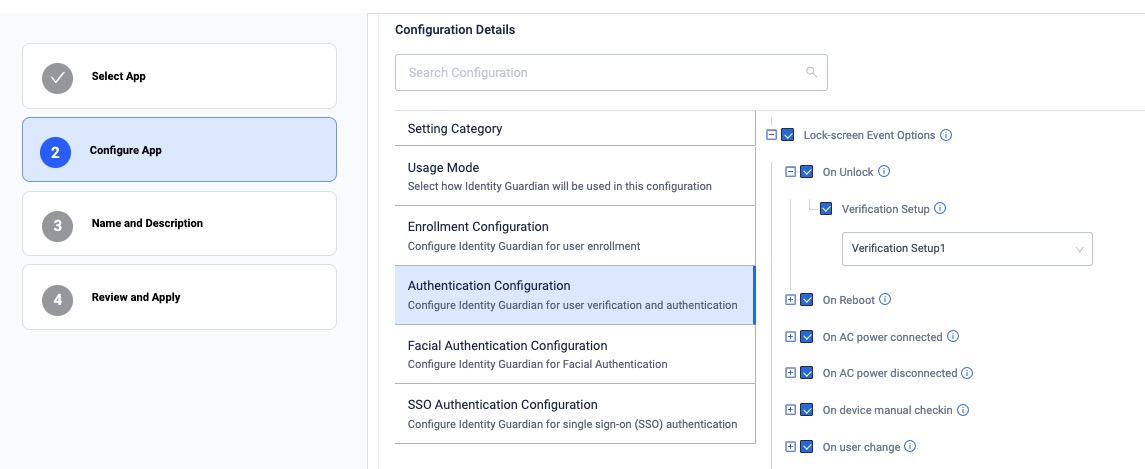 zDNA Cloud Managed Config
zDNA Cloud Managed Config
Configure the SSO Authentication Configuration for the app to communicate with Microsoft SSO to authenticate the user:
- Single Sign On Provider: Microsoft
- Authentication Protocol: OAuth 2.0 (OIDC)
- Scope: [Enter the string based on the SSO server settings]
- Configuration Settings: [Enter the following string, but replace "client_id" and "authority_url" with your values from
auth_config_single_account.jsonfile downloaded from step I.]{ "client_id" : "[ENTER YOUR CLIENT ID]", "authorization_user_agent" : "DEFAULT", "redirect_uri" : "msauth://com.zebra.mdna.els/KqmK9tYXpw%2BeW2lke7US3iG9EAQ%3D", "account_mode" : "SINGLE", "broker_redirect_uri_registered": true, "shared_device_mode_supported": true, "authorities" : [ { "type": "AAD", "authority_url": "[ENTER YOUR AUTHORITY URL]" } ] }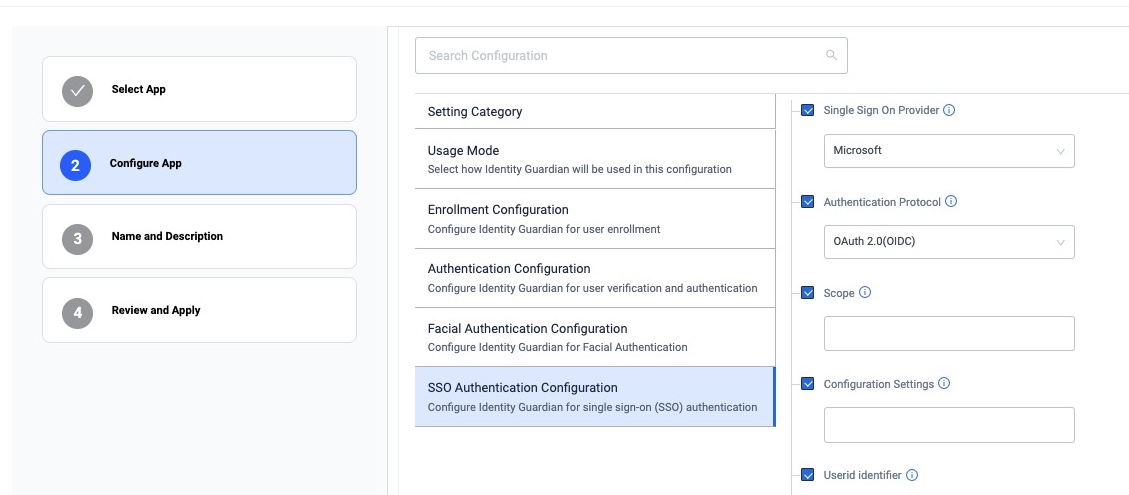 zDNA Cloud Managed Config
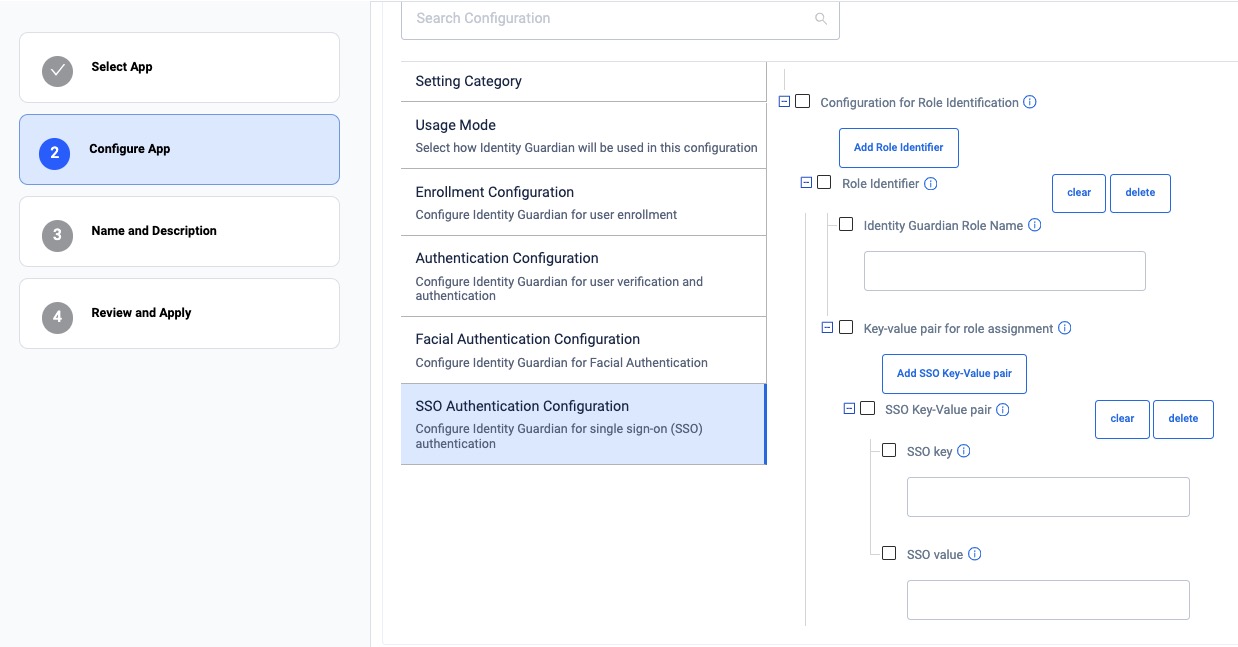
zDNA Cloud Managed Config If mapping the SSO response to application-specific roles, enter the following (see Managed Configurations for more information):
- Configuration Role Identification - Enables the recognition and mapping of the Single Sign-On (SSO) response to application-specific roles. Click Add Role Identifier as needed.
- Role Identifier - Establishes links between roles in SSO responses and their corresponding roles within the Identity Guardian app.
- Identity Guardian Role Name - Enter the Identity Guardian user role to be assigned based on SSO response during user sign-in
- Key-value Pair for Role Assignment - Add one or more SSO key-value pairs to identify and map users to a predefined Identity Guardian user role. Click Add SSO Key-Value Pair as needed.
- SSO Key-Value Pair - Choose whether the SSO response, which contains the user key and values, should be mapped to a corresponding user role in Identity Guardian
- SSO Key - Enter the SSO key to map it to an Identity Guardian role.
- SSO Value - Enter the SSO value(s) to map to the Identity Guardian role. Use commas to separate multiple entries.
 zDNA Cloud Managed Config
zDNA Cloud Managed Config See Managed Configurations to configure any other non-SSO settings.
Deploy the Managed Configurations to the devices through your EMM.
When a device gets updated with the new configurations, Zebra Identity Guardian activates the lock screen. The user is then required to authenticate themselves using Single Sign-On (SSO) to gain access to the device. See User Guide for more information.
PingID
This section provides guidance to integrate Identity Guardian with PingID.
To enable user access to the device through SSO, install and set up Identity Guardian on the devices:
- Deploy and install Zebra Identity Guardian app on the devices.
- Launch the app using an EMM. This step must be performed at least once.
- Enter the Managed Configuration settings for the app via your EMM:
- Select the application mode:
- Application Mode: Authentication
 zDNA Cloud Managed App Config
zDNA Cloud Managed App Config
- Application Mode: Authentication
- Configure the Verification Setup to validate the user access:
- Primary Authentication Factor: SSO
- Secondary Authentication Factor: [Select FACE, PASSCODE, or NO_COMPARISON]
- Fallback Authentication Factor: [Select FACE, PASSCODE, NONE, SSO or ADMIN BYPASS PASSCODE]
- Primary Authentication Timeout: [Enter value in ms, e.g. "300000"]
- Fallback Authentication Timeout: [Enter value in ms, e.g. "300000"]
 zDNA Cloud Managed Config
zDNA Cloud Managed Config
- Configure the Lock-screen Event options:
- On Unlock:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On Reboot:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On AC power connected:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On AC power disconnected:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On device manual check in:
- Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
- On user change: - Verification Setup: [Enter the desired authentication scheme, e.g. "Verification Setup1"]
 zDNA Cloud Managed Config
zDNA Cloud Managed Config
- Configure the SSO Authentication Configuration:
- Single Sign On Provider: PingId
- Authentication Protocol: OAuth 2.0 (OIDC)
- Scope: openid email profile
- Userid Identifier: [Specify the user key for identifying the signed-in user]
- Configuration Settings: [Enter the specified string, but replace the following values with those from your own SSO response: logoutURL, revokeURL, tokenURL, authorizationURL, clientId, userInfoUrl]
{ "redirectURI" : "com.zebra.mdna.els:/loginComplete", "logoutURL" : "[enter your logout URL]", "revokeURL" : "[enter your revoke URL]", "tokenURL" : "[enter your token URL]", "authorizationURL" : "[enter your authorization URL]", "clientAuthType" : 0, "clientId" : "[enter your clientID]", "certificatePhrase" : "", "userInfoUrl" : "[enter your userInfo URL]", "certificate" : "" }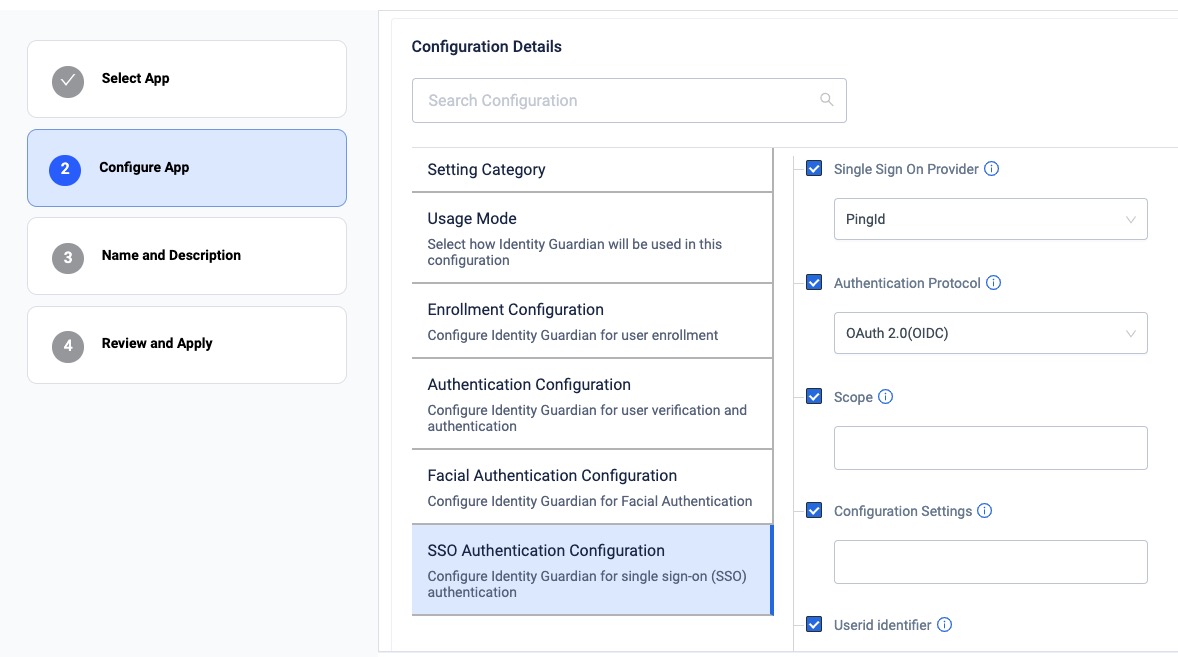 zDNA Cloud Managed App Config
zDNA Cloud Managed App Config
- Select the application mode:
- If mapping the SSO response to application-specific roles, enter the following (see Managed Configurations for more information):
- Configuration Role Identification - Enables the recognition and mapping of the Single Sign-On (SSO) response to application-specific roles. Click Add Role Identifier as needed.
- Role Identifier - Establishes links between roles in SSO responses and their corresponding roles within the Identity Guardian app.
- Identity Guardian Role Name - Enter the Identity Guardian user role to be assigned based on SSO response during user sign-in
- Key-value Pair for Role Assignment - Add one or more SSO key-value pairs to identify and map users to a predefined Identity Guardian user role. Click Add SSO Key-Value Pair as needed.
- SSO Key-Value Pair - Choose whether the SSO response, which contains the user key and values, should be mapped to a corresponding user role in Identity Guardian
- SSO Key - Enter the SSO key to map it to an Identity Guardian role.
- SSO Value - Enter the SSO value(s) to map to the Identity Guardian role. Use commas to separate multiple entries.
 zDNA Cloud Managed Config
zDNA Cloud Managed Config
- Configuration Role Identification - Enables the recognition and mapping of the Single Sign-On (SSO) response to application-specific roles. Click Add Role Identifier as needed.
- See Managed Configurations to configure any other non-SSO settings.
- Deploy the Managed Configurations to the devices through your EMM.
When a device gets updated with the new configurations, Zebra Identity Guardian activates the lock screen. The user is then required to authenticate themselves using Single Sign-On (SSO) to gain access to the device. See User Guide for more information.
Secure Setup for Faster Logins
Identity Guardian can simplify Single Sign-On (SSO) logins by prompting users for SSO authentication only once, post device enrollment. For frequent situations like device lock, it offers efficient options like biometric or pin-based access, eliminating the need for repeated SSO logins. It maintains the original SSO session's integrity, ensuring exclusive user access and simultaneous logout from all apps, creating a secure and streamlined login process.
To implement this authentication strategy, follow the procedure below based on whether the device model is shared or personally assigned.
Shared Devices
Administrator setup - refer to Managed Configurations:
- Set SSO authentication in the following managed configurations:
- Usage Mode
- Application Mode: Authentication
- Authentication Configuration
- User Verification Methods
- Verification Setup1: [Select or enter all desired options and include SSO as one of the authentication factors.]
- Lock-screen Event Options
- On user change: [Select the verification that includes SSO authentication, e.g. Verification Setup1]
- Usage Mode
- For the rest of the following Lock-screen Event Options, select the verification that does not include SSO authentication, e.g. Verification Setup2 (includes face or passcode):
- On Unlock
- On Reboot
- On AC Power Connected
- On AC Power Disconnection
- In Authentication Configuration, set the following to false under Force Logout Options:
- On Lock
- On Reboot
- On AC Power Connected
- On AC Power Disconnected
End user authentication:
- Enroll the user. Make sure to enter the SSO user ID in the Employee ID field.
- Once the enrollment process is complete, the user is required to authenticate themselves on the device by scanning their user barcode once.
- If the scanned barcode matches with the enrolled user, the SSO session remains active. For subsequent logins, the user is prompted to authenticate via facial biometrics or user passcode, depending on the setup by the administrator.
- If the scanned barcode does not match with the enrolled user, it prompts for SSO credentials since an “On user change” event occurred. These SSO credentials remain active on the device.
- After the user authenticates, the user is no longer required to re-enter their SSO credentials unless one of the following occurs:
- The user logs out manually from the device
- The user is automatically logged out of the device if any of the Force Logout Options are met from Authentication Configuration in the managed configurations.
- The SSO session times out.
Personally Assigned Devices
Administrator setup - refer to Managed Configurations:
- Set SSO authentication in the following managed configurations:
- Usage Mode
- Application Mode: Personally Assigned
- Authentication Configuration
- User Verification Methods
- Verification Setup1: [Select or enter all desired options and include SSO as one of the authentication factors.]
- Lock-screen Event Options
- On user change: [Select the verification that includes SSO authentication, e.g. Verification Setup1]
- Usage Mode
- For the rest of the following Lock-screen Event Options, select the verification that does not include SSO authentication, e.g. Verification Setup2 (includes face or passcode):
- On Unlock
- On Reboot
- On AC Power Connected
- On AC Power Disconnection
- In Authentication Configuration, set the following to false under Force Logout Options:
- On Lock
- On Reboot
- On AC Power Connected
- On AC Power Disconnected
End user authentication:
- Enroll the user. Make sure to enter the SSO user ID in the Employee ID field.
- Once the enrollment process is complete, the user is required to authenticate themselves on the device by facial biometrics or passcode entry once. If successful, the SSO session remains active.
- After the user authenticates, the user is no longer required to re-enter their SSO credentials unless one of the following occurs:
- The user logs out manually from the device
- The user is automatically logged out of the device if any of the Force Logout Options are met from Authentication Configuration in the managed configurations.
- The SSO session times out.