Overview
This guide covers advanced EHS features such as Kiosk Mode and EHS Logging. It assumes a working knowledge of Enterprise Home Screen and use of its Advanced Settings through direct manipulation of the enterprisehomescreen.xml config file. For those not familiar with these procedures, please refer to the About and Setup pages and the Advanced Settings Guide before continuing.
Note: Many of the capabilities of EHS can be accomplished manually on the device, programmatically through EMDK or remotely using StageNow or a third-party Enterprise Mobile Management (EMM) system (if supported by that EMM system). EHS simply puts the capabilities into a single tool.
Note: Secure Mode is discontinued in EHS 3.0 and higher.
Kiosk Mode
Kiosk Mode is designed for devices to run a single application, often with a touch-based UI. Examples include retail price checkers, auto parts look-ups, patient check-in systems and so on. Kiosk Mode also can be useful when dedicating a device to a single user and/or task, such as a retail clerk's hand-held barcode scanner. Kiosk Mode places the app in full-screen mode and prevents the BACK and HOME keys from being used to exit the app by mapping those keys to the Kiosk app's most recent activity.
Also see the EHS Auto-Launch feature, which provides functionality similar to Kiosk Mode without changing the HOME and BACK key functions.
Kiosk Mode tags:
<kiosk> - Specifies the app that will run when Kiosk Mode is enabled
<kiosk_mode_enabled> - Toggles the feature on and off
Enable Kiosk Mode
In the enterprisehomescreen.xml file:
- Specify the Kiosk app in the <kiosk> section of the config file.
- Enter a value of '1' in the <kiosk_mode_enabled> tag in the Preferences section of the file.
- If USB Debugging is desired in Kiosk Mode, enter a value of '0' in the <usb_debugging_disabled> tag.
(See Disable Kiosk Mode below for details).
Security Note: When using Kiosk Mode, be sure to disable 'key remapping' and other possible methods of launching applications, which would thereby defeat Kiosk Mode safeguards.
Disable Kiosk Mode
Once Kiosk Mode is enabled it can be disabled in only one of two ways (without writing custom program code):
If USB Debugging was not disabled for User Mode, disable Kiosk Mode by pushing to the device a config file with a value of '0' in the <kiosk_mode_enabled> tag.
If USB Debugging was disabled for User Mode, perform a factory reset.
Control Kiosk Mode Programmatically
Kiosk Mode can be controlled from within an Android application using Android Intents. The following JavaScript code shows how to enable and disable Kiosk Mode programmatically:
//Disable Kiosk Mode:
Intent intent = new Intent("com.symbol.enterprisehomescreen.actions.MODIFY_KIOSK_MODE");
Intent.putExtra("enable",false);
sendBroadcast(intent);
//Enable Kiosk Mode:
Intent intent = new Intent("com.symbol.enterprisehomescreen.actions.MODIFY_KIOSK_MODE");
Intent.putExtra("enable",true);
sendBroadcast(intent);
Security Note: When using Kiosk Mode, be sure to disable "key remapping" and other possible methods of launching applications, which would thereby defeat Kiosk Mode safeguards.
Privileged Settings
In EHS 3.0 (and higher), certain features once automatically enabled when entering Admin Mode must now be enabled manually. EHS refers to these as Privileged Settings:
- USB debugging
- The Android Settings panel app
- The Google Search app
Most notably, activation of USB Debugging enables the Android Debug Bridge (adb) and its ability to transfer files to and from a device. The Privileged Settings state on the device is indicated by a pop-up whenever the user enters Admin Mode:
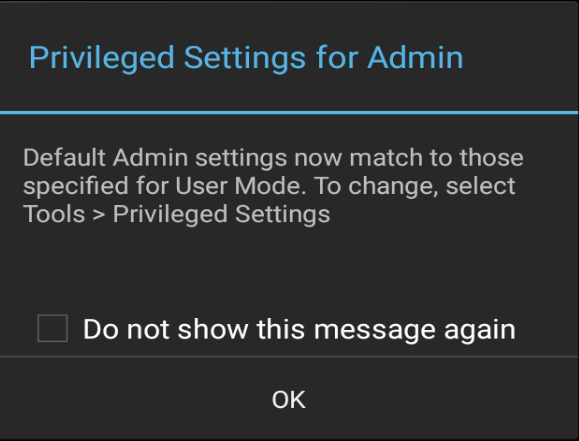 Tap "OK" to dismiss.
Tap "OK" to dismiss.
All three Privileged Settings are enabled as a group through an Admin-mode UI control and are disabled automatically when re-entering User Mode.
To access Privileged Settings:
- While in Admin Mode, go to Tools -> Privileged Settings for Admin:
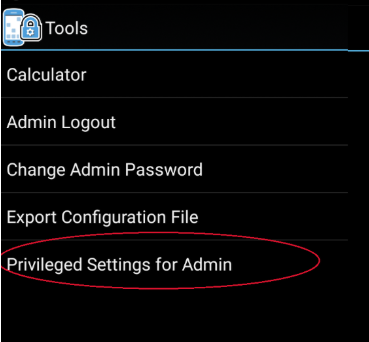
- The current state (disabled) is shown.
Tap "Enable" to activate Privileged Settings: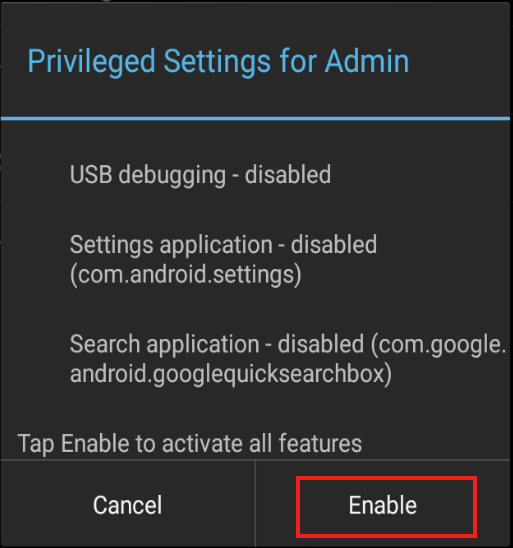
- Privileged Settings are enabled immediately. Tap "OK" to continue.
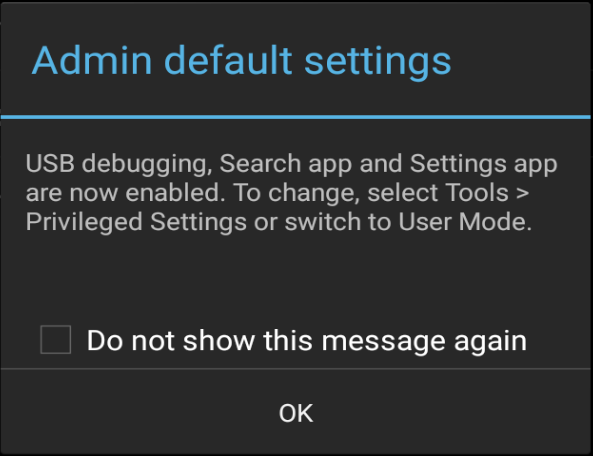
Administrator Note: Be sure to restore settings (to disable USB debugging, Settings app, Search app) once privileged-mode tasks are completed.
To disable Privileged Settings:
- Go to Tools -> Privileged Settings for Admin:

- The current state (enabled) is shown.
Tap "Restore" to disable all three features: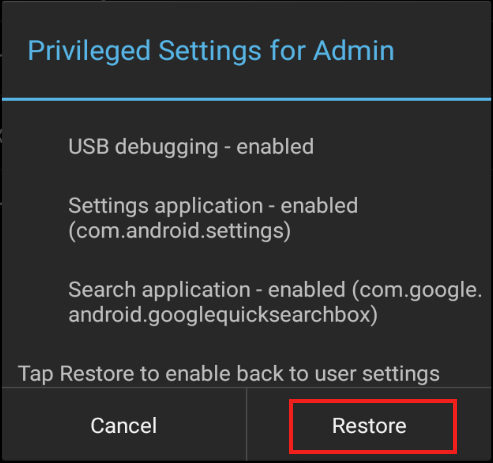
- Features are disabled immediately and a confirmation dialog appears.
Tap "OK" to continue.
EHS Log
EHS records all major activities, failures and security events in the /enterprise/usr/enterprisehomescreen.log file. These include failed attempts to enter Admin Mode, switches of the operating mode and all EHS errors. The log is a plain text file and can be retrieved with ADB or an EMM and viewed with any text editor.
For more information about logging, see Logging Preferences.
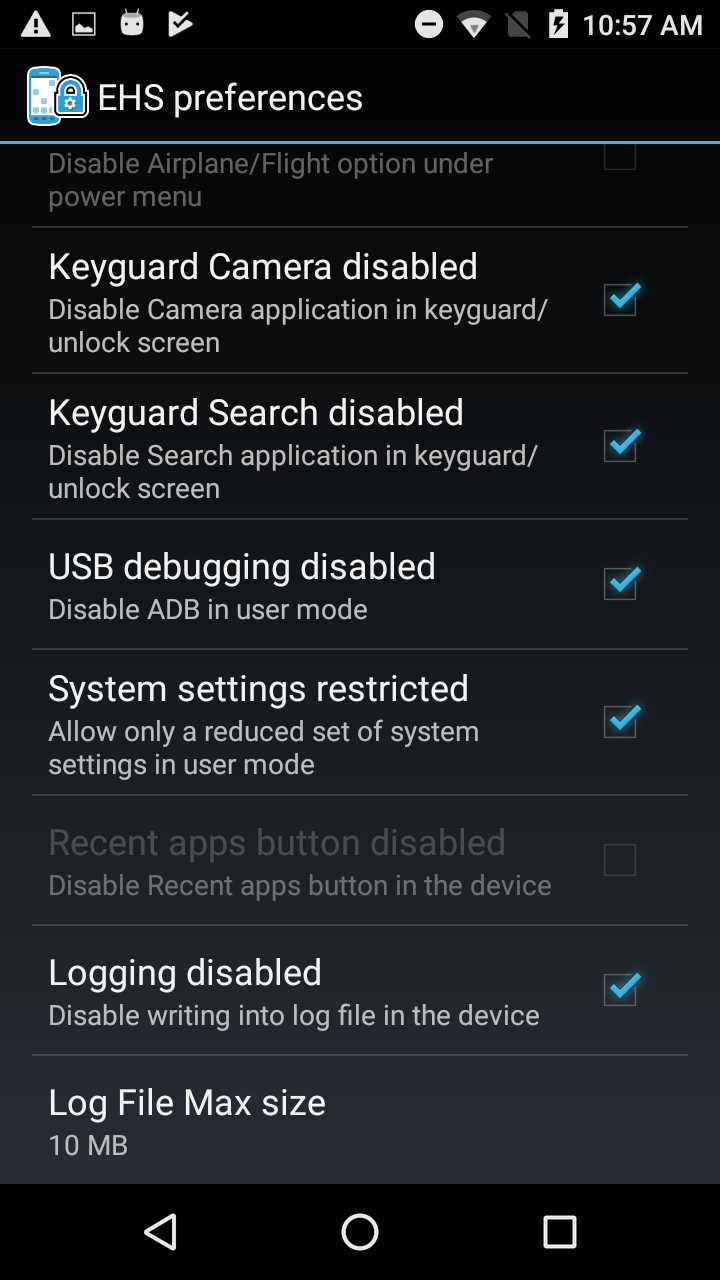 In EHS 2.7 and higher, logging can be enabled/disabled through the UI or config file.
In EHS 2.7 and higher, logging can be enabled/disabled through the UI or config file.
IMPORTANT: Secure Mode is discontinued in EHS 3.0 and higher. Log files are no longer designated as "SECURED" or "UNSECURED" in log entries.
Security Notes
This section covers important interactions between EHS and Android features that might impact device security or application behavior.
Recent Apps List
- Accessing an app from the Recent Apps list could represent a security risk; apps not cleared from the list can be activated with the BACK button, potentially exposing a non-EHS home screen.
- On Android Nougat and higher devices, the Recent Apps button can be Enabled/Disabled. It is disabled by default to prevent the use of multi-window mode.
- EHS does not add apps or activities to the Android Recent Apps list. However, apps/activities launched from within EHS could subsequently launch other apps/activities that could appear on the Recent Apps list and pose a security risk.
- Some devices retain the Recent Apps list after a reboot. Use App Manager through EMDK, StageNow or a third-party EMM system to clear the list.
- To manually clear Recent Apps, bring up the Recent Apps list by long-pressing the Home or Menu button (depending on the device) until the list appears, then swipe away each app.
Other Unintended Access
- Users might gain access to Airplane mode, Wi-Fi, Bluetooth and other device settings via the Quick Settings panel in the Notification drop-down even if Settings app is disabled by EHS. This can be prevented with settings configurable using the UI Manager through StageNow or EMDK.
- Wireless capabilities also can be individually disabled through these MX modules:
- SettingsMgr for Airplane Mode and Wi-Fi
- UiMgr for Quick Settings and the "Gear" icon
- WirelessMgr for Bluetooth, GPS, NFC and WWAN
- MX modules are accessible using EMDK or StageNow tools.
- Taking a screenshot (by pressing the "volume-down" and "Power" buttons simultaneously) while in User Mode might expose users to the Gallery app or to apps used for sharing images such as Gmail and MMS. To prevent this, disable such unwanted apps in the Disable/Enable Applications section of Optional Feature Tags section.
- If the Programmable Keys feature on the Android System Settings panel is used to program a key to launch an application, that key mapping will be available in User Mode.
Bluetooth User Access
EHS by default disables the Settings app (com.android.settings) when the device is in User Mode or Admin mode. This prevents the "BT Pairing Utility" from enabling Bluetooth and pairing with devices. For organizations that wish to allow this capability, EHS offers a means of enabling Bluetooth control while restricting access to most other Settings panel features.
To enable Bluetooth:
- Enable the Settings app using the Enable/Disable Apps feature.
- Enable the Restrict System Settings feature, which allows Bluetooth to be turned on and off while in User Mode.
The BT Pairing Utility now works as expected.
Note: The System Settings Restricted feature allows the device user to access Display and Sound settings and the "About device" screen.